据慢雾技术报道,最近,一些数字货币交易中心向慢雾安全团队报告,他们收到了勒索信息。勒索者向交易中心发送电子邮件或Telegram据报道,交易中心存在BUG,一旦被攻击,平台将无法打开。如果你想得到它BUG报告需要向指定地址支付BTC。然而,许多交易中心表示支付BTC之后,对方只发送了初步信息BUG报告或没有回应。
慢雾合伙人兼安全负责人海盗王告诉巴比特,“目前,已有5家交易中心向我们报告了这种情况敲诈者使用不同的电子邮件或Telegram ID,向交易中心相关负责人发送勒索邮件,勒索金额为0.1BTC至2BTC不同,使用不同BTC地址。”
截至出版,据不完全统计,敲诈者Telegram ID有@zed1331、@bbz12、@samzzcyber,邮箱有mikemich@protonmail.com,BTC地址有3GQQt2zJnPAWvirym7pbwvNTeM5igGuKxy,地址入账约43.45个BTC(约40.41万美元),如下图所示。
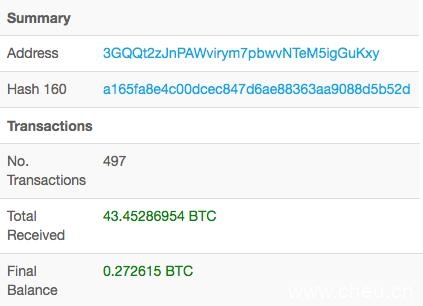
截图自Blockchain.com
海盗王向巴比特提供了诈骗邮件的原文(如文末附录所示),邮件称,“交易中心存在‘Web服务整形溢出’BUG,一旦被攻击,就会导致Web服务器崩溃,无法访问…..我们可以解决这个问题BUG问题……若要获取BUG需要支付两份报告BTC指定地址。”
值得注意的是,邮件还指出,“截至2019年3月1日,奖励机构包括KuCoin、CoinSwitch、Phantasma、PlatonFinance、Vulnerability Analysis、 STEX Exchange、XCOYNZ Project等。”
海盗王向巴比特透露,在与KuCoin交易中心相关负责人取得联系后,负责人表示确实有Telegram用户反映BUG但是KuCoin并未支付2BTC赏金,提醒大家不要相信骗子。
截图由KuCoin提供相关负责人
还有一类与Linkedin相关的钓鱼邮件,大致内容如下:
Hey,We have found a nefty integer overflow vulnerability on=> https://www.xxx.com
Attacker could alter webserver. I have experience working to upgrade security for large exchanges,like xxx,and would like to propose about this.
May we go on to demonstrate this vuln?
You can verify me as an security researcher on LinkedIn as follows:=> https://www.linkedin.com/in/xxxxx/
海盗王分析说,“邮件包含一个 Linkedin因为在,链接Linkedin 需要在平台上登录个人账户查看个人信息,所以当交易中心的工作人员登录自己的 Linkedin 账号,查看提交BUG 人员(可能是钓鱼攻击者) Linkedin 账户信息时,攻击者还可以查看交易中心工作人员的信息,从而获取其他社交平台信息。”
近年来,数字货币市场的资金数量呈井喷式爆发,安全风险主要是交易市场操纵风险、交易平台风险、欺诈风险和钱包风险。
除上述电子邮件钓鱼攻击外,其他类型的钓鱼攻击包括域名钓鱼(使用类似官方网站的网站)Twitter 1 for 10(支付0.5-10ETH返利5-100ETH)、假APP和假工作人员等。
所谓“钓鱼攻击”,通过电子邮件、通信软件、社交媒体等方式,攻击者伪装成可信的人或机构,获取用户名、密码、私钥等私人信息。
海贼王认为,此次邮件钓鱼攻击事件中,部分交易中心之所上述当受骗,主要由于交易中心缺少专业的安全BUG判断能力和信息孤立导致它无法处理当前的情况BUG准确判断整体情况。
“无论对方是否真的发现了交易中心BUG,只要价格合适,就愿意花钱赌博。如果赌对了,交易中心可以少曝光一次。BUG公关危机,平台被攻击的可能性至少一次;如果你输了,损失不多,你可以承受。骗子利用了交易中心的心理。”
他建议,
“首先,不要打开攻击者发送的任何链接或文件,可能有木马病毒;其次,攻击者没有确切通知BUG在细节之前,不要攻击者BTC;最后,如果交易中心不能准确判断和单独处理,可以联系安全公司协助处理。”
附(钓鱼邮件原文):
It's more like an vulnerability which allows an attacker to crash the webserver of the following website. "Integer -overflow" related. The attack vector itself holds a huge security risk,when exploited,the webserver could crash due to it,and eventually be unreachable. The flaw has been done through exploitable web elements on your website.
Our proposal is based on information-security (infosec) regarding cybersecurity.
Confidentiality: assist infosec wisely to implement firewalls,intrusion detectors and prevention technologies to ensure reliable provided service. (not actual server access required.)
Availability: In order to ensure that I would have infosecurity on redundancy and backups,next to every "to be addressed" phase;
We have added in a short meaning on what does it include as can be seen.
• The audit process 1.1 Audit planning & preparation 1.2 Establishing audit objectives 1.3 Performing the review 1.4 Issuing the review report
• The audit System 2.1 Networking Security 2.2 Backend Installation / Security 2.3 API Audition 2.4 CDN Anti malicious attacks protection 2.5 Code Audit: checking vulnerability in any PHP / ASP / JS code
Vouches by companies:
[Make sure to check the provided link for vouch.]
1. KuCoin=>{ https://i.imgur.com/y0AXMCn.jpg ]
2. CoinSwitch=> https://i.imgur.com/l8D8g9p.jpg ]
CoinSwitch Contract example=> https://i.imgur.com/P2hMNxD.jpg
3. Phantasma=> https://i.imgur.com/y1QCOuL.jpg ]
4. PlatonFinance=> https://i.imgur.com/189Ejdz.jpg ]
5. Vulnerability Analysis (just an example)
=>https://i.imgur.com/V0C19KZ.jpg
and many more.
6. STEX Exchange paid 3 BTC for our infosec and analysis:=> https://m.imgur.com/18tAXah
7. Proof of Kucoin Payment to us:https://i.imgur.com/trBbVKP.jpg
8. XCOYNZ Project:https://i.imgur.com/UbUliaI.jpg
Proof of compensations: Different companies which some included be seen in multiple vouches above,
when/if 新手炒币入门基础知识图谱 one of the servers is down,the second server would replace it and ensure that the services are up and running without any downtime.
General knowledge=> This type of attack as demonstraded are based on exploiting website elements: these can include forms,direct webserver exploit,or DNS leaking for the actual backend server,which gives an malicious attacker multiple chances to work with.
We'd address the required knowledge needed to counter this type of threats.
These following items listed below are our main focuses what we will send reports to regarding,
have rewarded me almost total of [$ 102,783.91 USD on 01/03/2019 rate for security related bounties, cybersecurity, demonstrations, and different VA reports.
Blockchain URL:=>https://www.blockchain.com/btc/address/3GQQt2zJnPAWvirym7pbwvNTeM5igGuKxy
Pricing for the Infosec/Audit offered:=> 2 BTC
To make it clear the price will be one-time payment and afterwards there won't be any charge. You can consult us further at anytime.




